Real-time is the future for data logger solutions. An in-time report is valuable for decision-makers during transportation.
In this article, we are going to explain how real-time data logger works to push data online.
Building connections
We are talking about wireless connection, nowadays we have WIFI, Bluetooth, Zigbee, RF etc, but they are all restricted by distance. Therefor in a typical cross border real-time data logger, cellular technology is used for data transmission, in particular, GSM.
We build GSM modem in every data logger, together with an embedded global sim card. Both the modem standards and the sim card operator will decide the data connection coverage. Take Cydiance Lorca/Piura for example, the device enables coverage of more than 160 countries, check the list here.
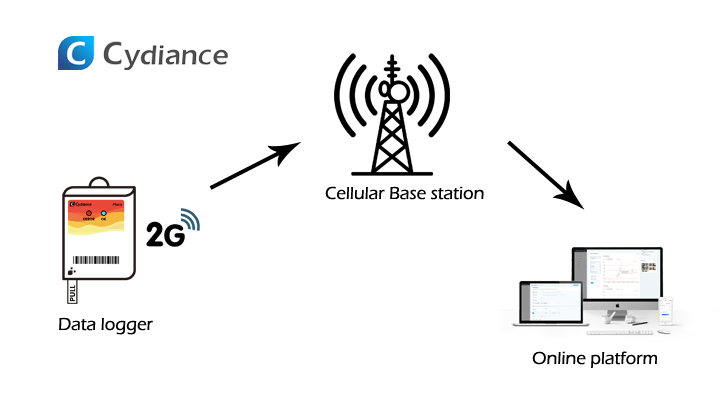
You may well ask why do we not use 4G but 2G, a simple reason is 4G modem is much more expensive than 2G, especially in our single-use scenarios. There are also other cons with regards to 4G, we will write another article for this topic.
Connection exceptions
In this GSM model, the device will lose connection when there’s no base station around, for example travelling across oceans, this is a problem that basically can’t be solved. Unless we get a connection via satellite, but apparently the cost is way too high.
Data processing and storage
We will store all data sent by the device. In a later stage(it happens normally in several seconds) the system will proceed to data filtering, duplicates removing, etc., based on some complex algorithms. Refined data will then be presented on webpages.
Data security
We encrypt all transferring data from the device and also exchanges between servers. We store data in high standard data centres which comply with GDPR, and with enhanced security strategy to withstand external attacks.



